OverTheWire-Bandit 靶场
OverTheWire Bandit 靶场
https://overthewire.org/wargames/bandit
Level 0
The goal of this level is for you to log into the game using SSH. The host to which you need to connect is bandit.labs.overthewire.org, on port 2220. The username is bandit0 and the password is bandit0. Once logged in, go to the Level 1 page to find out how to beat Level 1.
1 | ssh bandit0@bandit.labs.overthewire.org -p 2220 |
Level 1
1 | boJ9jbbUNNfktd78OOpsqOltutMc3MY1 |
The password for the next level is stored in a file called - located in the home directory
1 | cat ./- |
Level 2
1 | CV1DtqXWVFXTvM2F0k09SHz0YwRINYA9 |
The password for the next level is stored in a file called spaces in this filename located in the home directory
1 | cat "spaces in this filename" |
Level 3
1 | UmHadQclWmgdLOKQ3YNgjWxGoRMb5luK |
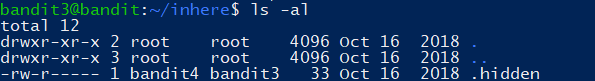
The password for the next level is stored in a hidden file in the inhere directory.
1 | cat ./inhere/.hidden |
Level 4
1 | pIwrPrtPN36QITSp3EQaw936yaFoFgAB |
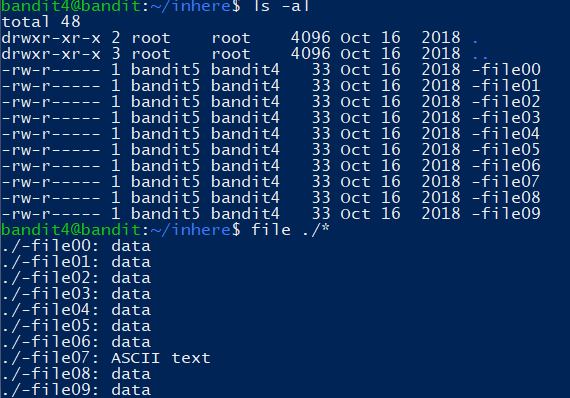
The password for the next level is stored in the only human-readable file in the inhere directory. Tip: if your terminal is messed up, try the “reset” command.
1 | cat ./inhere/-file07 |
Level 5
Level Goal
The password for the next level is stored in a file somewhere under the inhere directory and has all of the following properties:
- human-readable
- 1033 bytes in size
- not executable
1 | koReBOKuIDDepwhWk7jZC0RTdopnAYKh |
du 命令
1 | -a或-all 显示目录中个别文件的大小。 |

Level 6
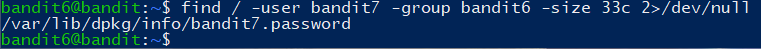
The password for the next level is stored somewhere on the server and has all of the following properties:
- owned by user bandit7
- owned by group bandit6
- 33 bytes in size
1 | DXjZPULLxYr17uwoI01bNLQbtFemEgo7 |
find 命令
1 | -user 指定所有者 |
错误信息隐藏:2>/dev/null
Level 7
The password for the next level is stored in the file data.txt next to the word millionth
1 | HKBPTKQnIay4Fw76bEy8PVxKEDQRKTzs |
1 | vi data.txt |
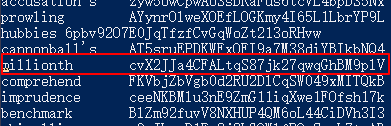
或者利用 grep
Level 8
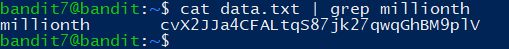
The password for the next level is stored in the file data.txt and is the only line of text that occurs only once
1 | cvX2JJa4CFALtqS87jk27qwqGhBM9plV |
sort命令
1 | 文本排序sort |
uniq命令
1 | uniq -c 显示没行重复出现的次数 |
Level 9
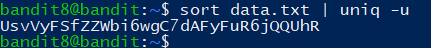
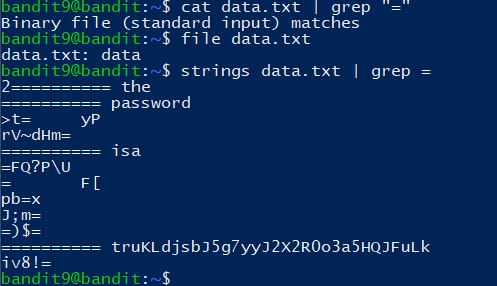
The password for the next level is stored in the file data.txt in one of the few human-readable strings, beginning with several ‘=’ characters.
1 | UsvVyFSfZZWbi6wgC7dAFyFuR6jQQUhR |
Level 10
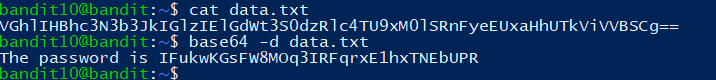
The password for the next level is stored in the file data.txt, which contains base64 encoded data
1 | truKLdjsbJ5g7yyJ2X2R0o3a5HQJFuLk |
Level 11
The password for the next level is stored in the file data.txt, where all lowercase (a-z) and uppercase (A-Z) letters have been rotated by 13 positions
1 | IFukwKGsFW8MOq3IRFqrxE1hxTNEbUPR |
Rot13编码:
1 | s="Gur cnffjbeq vf 5Gr8L4qetPEsPk8htqjhRK8XSP6x2RHh" |
Level 12
The password for the next level is stored in the file data.txt, which is a hexdump of a file that has been repeatedly compressed. For this level it may be useful to create a directory under /tmp in which you can work using mkdir. For example: mkdir /tmp/myname123. Then copy the datafile using cp, and rename it using mv (read the manpages!)
1 | 5Te8Y4drgCRfCx8ugdwuEX8KFC6k2EUu |
xxd 转换十六进制为二进制:
1 | xxd -r file new_file |
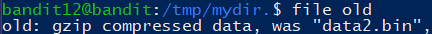
重命名追加 .gz
1 | gzip -d old.gz |
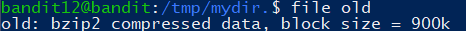
重命名追加 .bz2
1 | bzip2 -d old.bz2 |
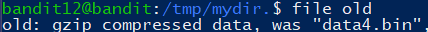
重命名追加 .gz,解压
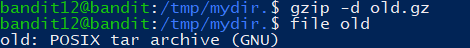
追加 .tar,
1 | tar -xf old.tar |
继续n重解压….
一直解压到 data8 得到密码
Level 13
The password for the next level is stored in /etc/bandit_pass/bandit14 and can only be read by user bandit14. For this level, you don’t get the next password, but you get a private SSH key that can be used to log into the next level. Note: localhost is a hostname that refers to the machine you are working on
1 | 8ZjyCRiBWFYkneahHwxCv3wb2a1ORpYL |
在用户当前用户家目录下有一个 sshkey.private 文件,保存到本地后利用它可登陆 bandit14 用户
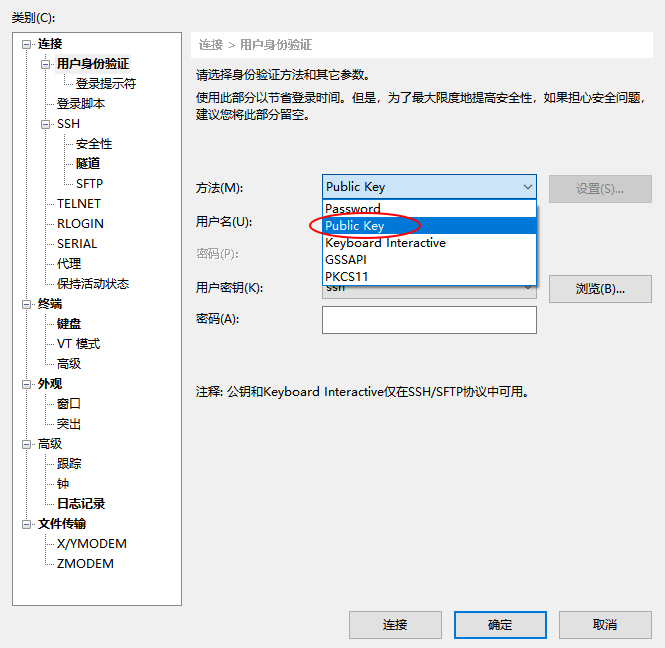
选择 public key 后点浏览-导入选择密钥文件,连接即可
或者是:
1 | ssh bandit14@bandit.labs.overthewire.org -p 2220 -i ssh.key |
Level 14
1 | 4wcYUJFw0k0XLShlDzztnTBHiqxU3b3e |
The password for the next level can be retrieved by submitting the password of the current level to port 30000 on localhost.
1 | nc localhost 30000 |
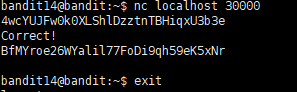
Level 15
1 | BfMYroe26WYalil77FoDi9qh59eK5xNr |
The password for the next level can be retrieved by submitting the password of the current level to port 30001 on localhost using SSL encryption.
Helpful note: Getting “HEARTBEATING” and “Read R BLOCK”? Use -ign_eof and read the “CONNECTED COMMANDS” section in the manpage. Next to ‘R’ and ‘Q’, the ‘B’ command also works in this version of that command…
1 | ncat localhost 30001 --ssl |
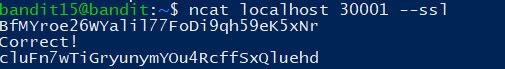
Level 16
1 | cluFn7wTiGryunymYOu4RcffSxQluehd |
The credentials for the next level can be retrieved by submitting the password of the current level to a port on localhost in the range 31000 to 32000. First find out which of these ports have a server listening on them. Then find out which of those speak SSL and which don’t. There is only 1 server that will give the next credentials, the others will simply send back to you whatever you send to it.
nmap 扫描指定端口:
1 | nmap -p31000-32000 127.0.0.1 |
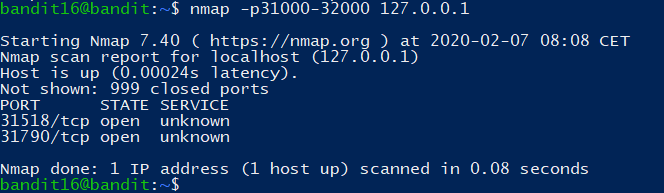
探测端口开放的服务:
1 | nmap -p31518,31790 -sV 127.0.0.1 |
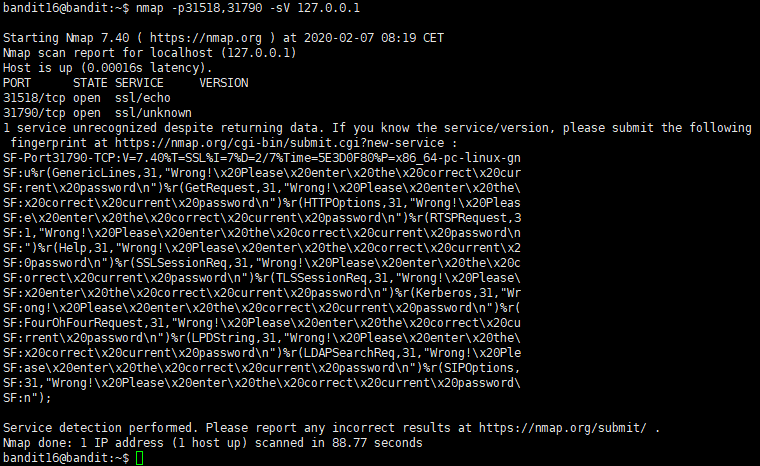
根据反馈结果判定是 31790 端口
1 | ncat localhost 31790 --ssl |
发送当前关密码得到下一关的登录密钥
Level 17
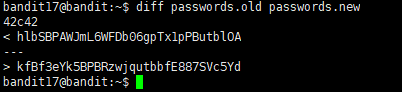
There are 2 files in the homedirectory: passwords.old and passwords.new. The password for the next level is in passwords.new and is the only line that has been changed between passwords.old and passwords.new
NOTE: if you have solved this level and see ‘Byebye!’ when trying to log into bandit18, this is related to the next level, bandit19
diff 命令
比较文件的差异:
1 | diff passwords.old passwords.new |
Level 18
1 | kfBf3eYk5BPBRzwjqutbbfE887SVc5Yd |
The password for the next level is stored in a file readme in the homedirectory. Unfortunately, someone has modified .bashrc to log you out when you log in with SSH.
1 | ssh bandit18@bandit.labs.overthewire.org -p 2220 "cat readme" |
Level 19
1 | IueksS7Ubh8G3DCwVzrTd8rAVOwq3M5x |
To gain access to the next level, you should use the setuid binary in the homedirectory. Execute it without arguments to find out how to use it. The password for this level can be found in the usual place (/etc/bandit_pass), after you have used the setuid binary.
该程序能够以bandit20的身份执行命令,查看密码
1 | ./bandit20-do cat /etc/bandit_pass/bandit20 |
Level 20
1 | GbKksEFF4yrVs6il55v6gwY5aVje5f0j |
There is a setuid binary in the homedirectory that does the following: it makes a connection to localhost on the port you specify as a commandline argument. It then reads a line of text from the connection and compares it to the password in the previous level (bandit20). If the password is correct, it will transmit the password for the next level (bandit21).
NOTE: Try connecting to your own network daemon to see if it works as you think
tmux 常用快捷键:
1 | Ctrl+B " 横向分割窗口 |
一边用 nc 监听端口,另一边使用程序连接端口:
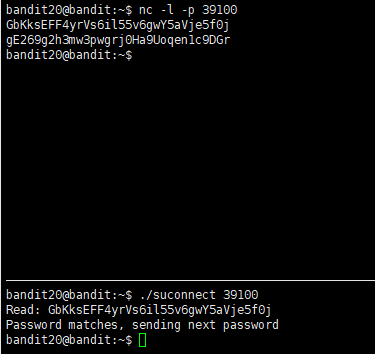
Level 21
1 | gE269g2h3mw3pwgrj0Ha9Uoqen1c9DGr |
A program is running automatically at regular intervals from cron, the time-based job scheduler. Look in /etc/cron.d/ for the configuration and see what command is being executed.
进入
etc/cron.d目录: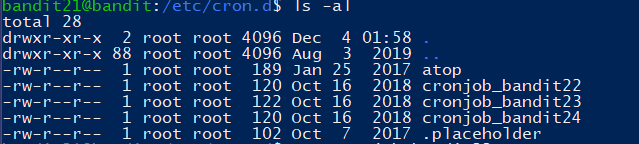
查看
cronjob_bandit22文件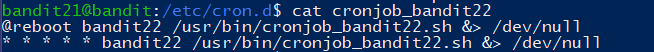
查看脚本文件:
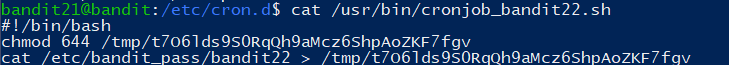
该任务是将 bandit22 的密码写入 tmp 目录下一个文件中,读取即可得到密码
Level 22
1 | Yk7owGAcWjwMVRwrTesJEwB7WVOiILLI |
A program is running automatically at regular intervals from cron, the time-based job scheduler. Look in /etc/cron.d/ for the configuration and see what command is being executed.
NOTE: Looking at shell scripts written by other people is a very useful skill. The script for this level is intentionally made easy to read. If you are having problems understanding what it does, try executing it to see the debug information it prints.
同上,查看脚本:
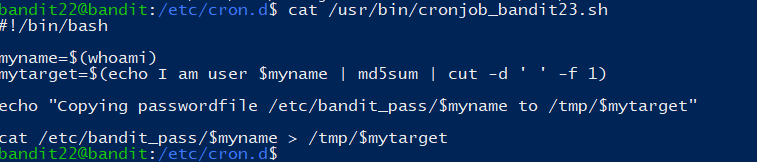
分析获取文件名:
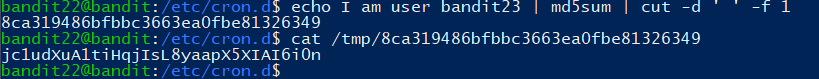
Level 23
1 | jc1udXuA1tiHqjIsL8yaapX5XIAI6i0n |
A program is running automatically at regular intervals from cron, the time-based job scheduler. Look in /etc/cron.d/ for the configuration and see what command is being executed.
NOTE: This level requires you to create your own first shell-script. This is a very big step and you should be proud of yourself when you beat this level!
NOTE 2: Keep in mind that your shell script is removed once executed, so you may want to keep a copy around…
前部分操作一致,查看脚本:
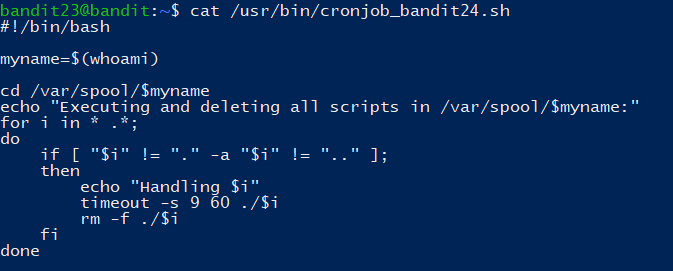
复制上一关的脚本即可,在/var/spool/bandit24 目录下任意创建一个脚本文件,保存内容为:
1 |
|
后续操作同上一关
Level 24
1 | UoMYTrfrBFHyQXmg6gzctqAwOmw1IohZ |
A daemon is listening on port 30002 and will give you the password for bandit25 if given the password for bandit24 and a secret numeric 4-digit pincode. There is no way to retrieve the pincode except by going through all of the 10000 combinations, called brute-forcing.
这一关需要编写 shell 脚本进行爆破
1 | c=UoMYTrfrBFHyQXmg6gzctqAwOmw1IohZ |
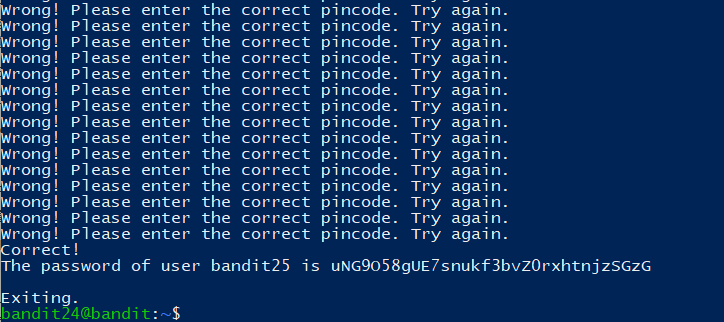
Level 25
1 | uNG9O58gUE7snukf3bvZ0rxhtnjzSGzG |
Logging in to bandit26 from bandit25 should be fairly easy… The shell for user bandit26 is not /bin/bash, but something else. Find out what it is, how it works and how to break out of it.
根据提示,查看 /etc/passwd
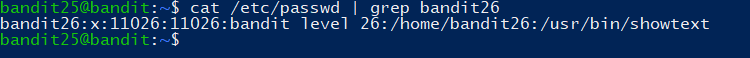
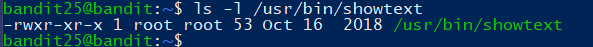
查看该文件:
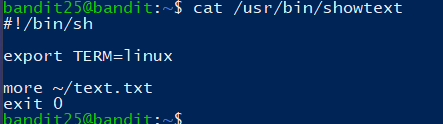
另外在bandit25家目录下有bandit26.sshkey文件
直接连接的话连接直接会断开:
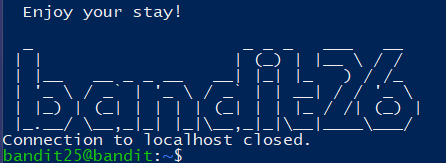
再回看脚本,可利用more的特性,将终端高度调整到最小再连接:
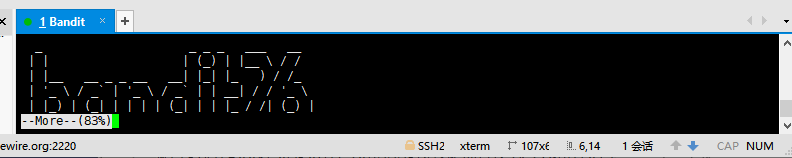
然后按 v 进入vi编辑器
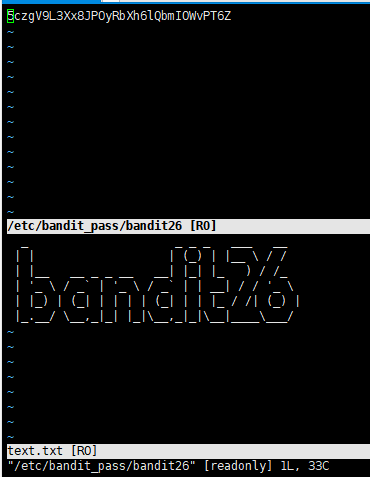
然后通过vi编辑器打开我们需要的 bandit26 的密码
这里用到vi打开文件:
- 在vi打开一个文件的时候,在命令行模式下可通过输入
sp filename分屏打开另一个文件(sp=split,vsp=vsplit) [切换窗口 Ctrl+ww]
Level 26
1 | 5czgV9L3Xx8JPOyRbXh6lQbmIOWvPT6Z |
Good job getting a shell! Now hurry and grab the password for bandit27!
同样通过more进入vi
不过没有权限通过 :. w !ls 之类的执行shell命令,需要设置一个shell
1 | :set shell=/bin/bash |
Level 27
1 | 3ba3118a22e93127a4ed485be72ef5ea |
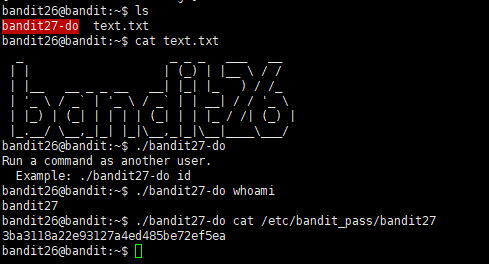
There is a git repository at
ssh://bandit27-git@localhost/home/bandit27-git/repo. The password for the userbandit27-gitis the same as for the userbandit27.Clone the repository and find the password for the next level.
Git 常用命令:https://blog.csdn.net/lxw198902165221/article/details/89228458
1 | git clone ssh://bandit27-git@localhost/home/bandit27-git/repo /tmp/repo_t |
Level 28
1 | 0ef186ac70e04ea33b4c1853d2526fa2 |
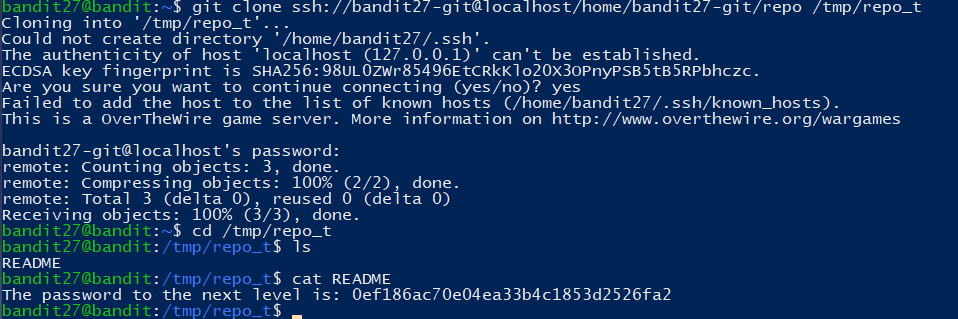
There is a git repository at
ssh://bandit28-git@localhost/home/bandit28-git/repo. The password for the userbandit28-gitis the same as for the userbandit28.Clone the repository and find the password for the next level.
同上一关的操作:
不过密码被隐藏了,git log 查看日志:
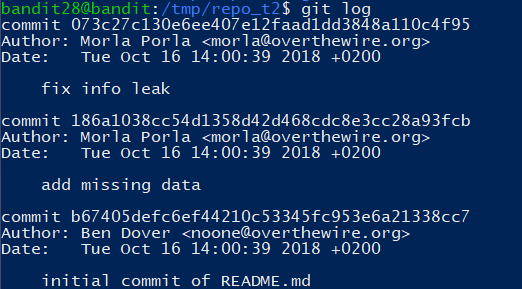
git show 默认会有 git diff -tree --cc 的格式,可以查看文本的差异
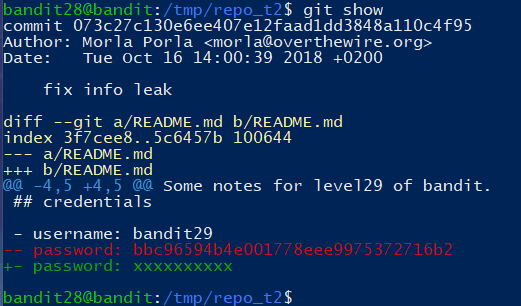
Level 29
1 | bbc96594b4e001778eee9975372716b2 |
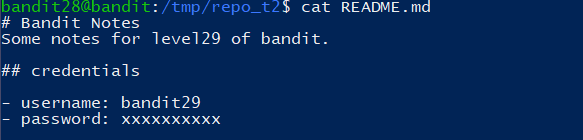
There is a git repository at
ssh://bandit29-git@localhost/home/bandit29-git/repo. The password for the userbandit29-gitis the same as for the userbandit29.Clone the repository and find the password for the next level.
按照之前的操作一遍,结果什么都没有,查看所有分支:
1 | git branch -a |
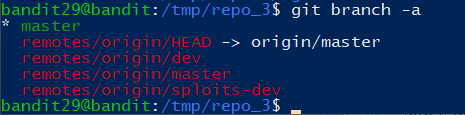
选择其中一个分支:
1 | git checkout -b remotes/origin/dev |
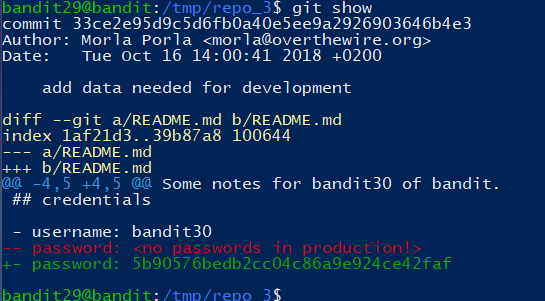
Level 30
1 | 5b90576bedb2cc04c86a9e924ce42faf |
There is a git repository at
ssh://bandit30-git@localhost/home/bandit30-git/repo. The password for the userbandit30-gitis the same as for the userbandit30.Clone the repository and find the password for the next level.
重复上一关操作,发现只有一个分支,没有其他有用的数据
1 | git show-ref # 显示本地引用 |
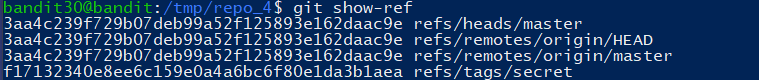
1 | git show f17132340e8ee6c159e0a4a6bc6f80e1da3b1aea |
得到密码
Level 31
1 | 47e603bb428404d265f59c42920d81e5 |
There is a git repository at
ssh://bandit31-git@localhost/home/bandit31-git/repo. The password for the userbandit31-gitis the same as for the userbandit31.Clone the repository and find the password for the next level.
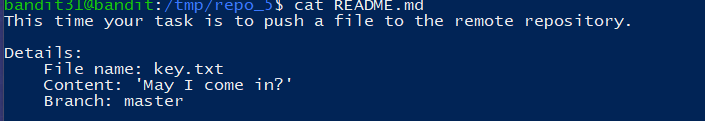
这一次需要往仓库push一个文件,命名为 key.txt,内容为 May I come in?
创建好文件后把它加入缓冲区:
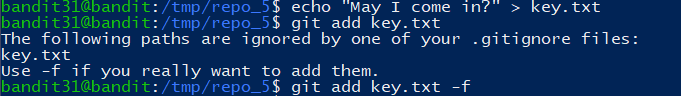
提交修改到仓库:
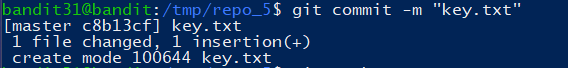
推送到仓库,得到密码:
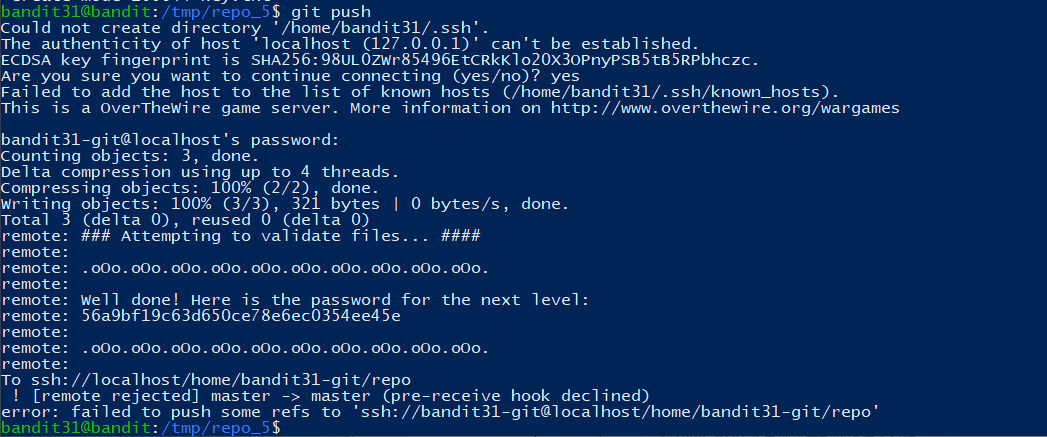
Level 32
1 | 56a9bf19c63d650ce78e6ec0354ee45e |
After all this
gitstuff its time for another escape. Good luck!
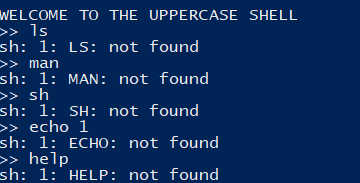
所有指令都变为了大写,这里就用到 shell 的特殊变量:
shell 特殊变量:
| 变量 | 含义 |
|---|---|
$0 |
当前脚本的文件名 |
$n |
传递给脚本或函数的参数。n 是一个数字,表示第几个参数。例如,第一个参数是$1,第二个参数是$2。 |
$# |
传递给脚本或函数的参数个数。 |
$* |
传递给脚本或函数的所有参数。 |
$@ |
传递给脚本或函数的所有参数。被双引号(“ “)包含时,与 $* 稍有不同,下面将会讲到。 |
$? |
上个命令的退出状态,或函数的返回值。 |
$$ |
当前Shell进程ID。对于 Shell 脚本,就是这些脚本所在的进程ID。 |
执行 $0 即相当于执行 sh
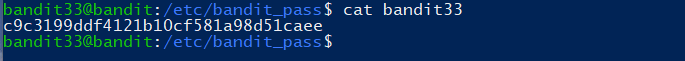
Level 33
1 | c9c3199ddf4121b10cf581a98d51caee |
At this moment, level 34 does not exist yet.