2023 山东省大学生网络安全技能大赛 复盘
2023 网安省赛复盘
前言
- AiDai👴🏻🐂🍺
Misc - 签到
下载附件得到游戏地址,随便玩了三四关发现一共 17 关,👴🏻懒的打了,网页源码中发现注释的 index.js,搜 flag 有个 flag 函数,里头就有 flag:
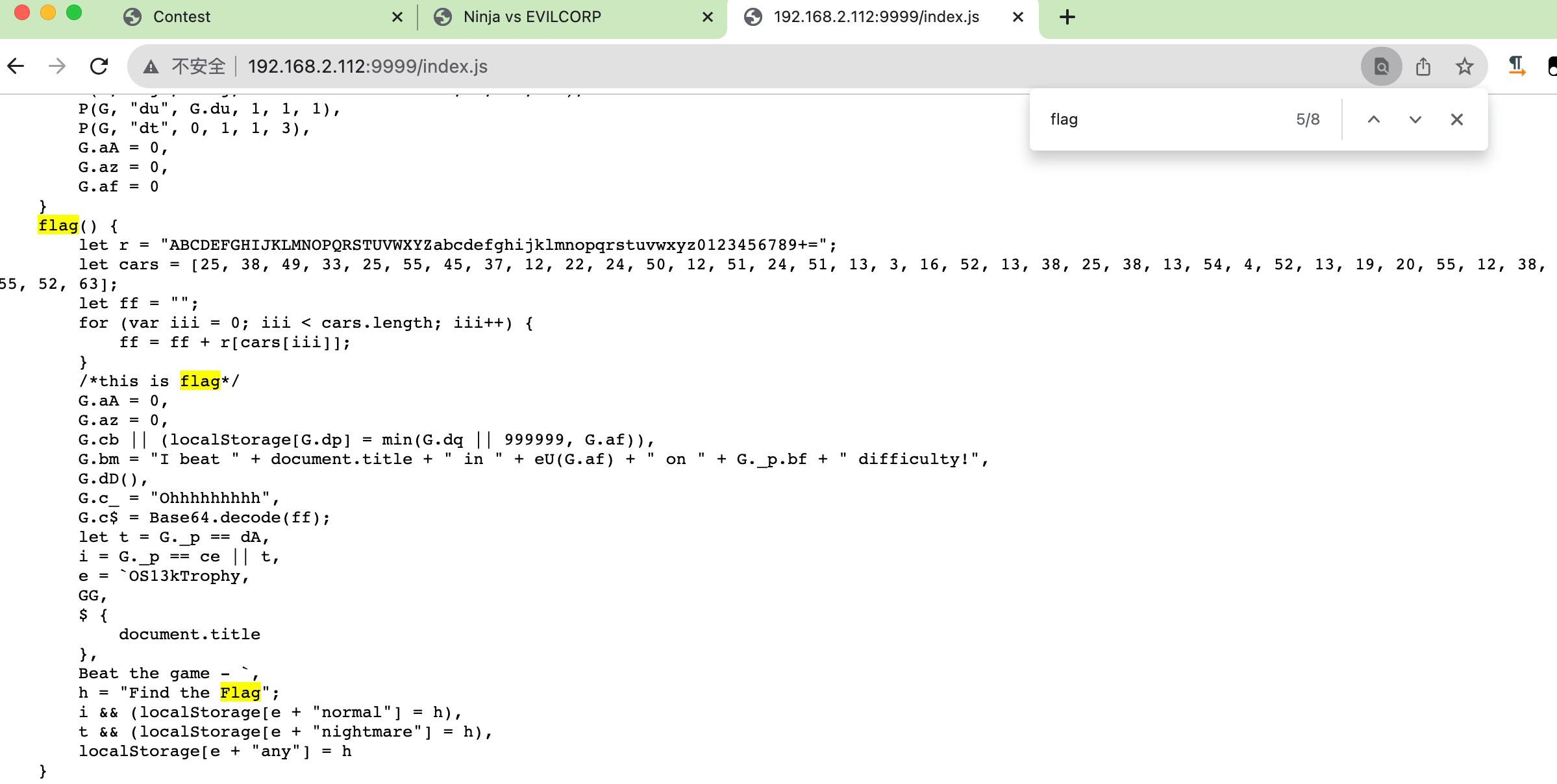
1 | let r = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+="; |
扔到控制台里头🏃🏻♀️:
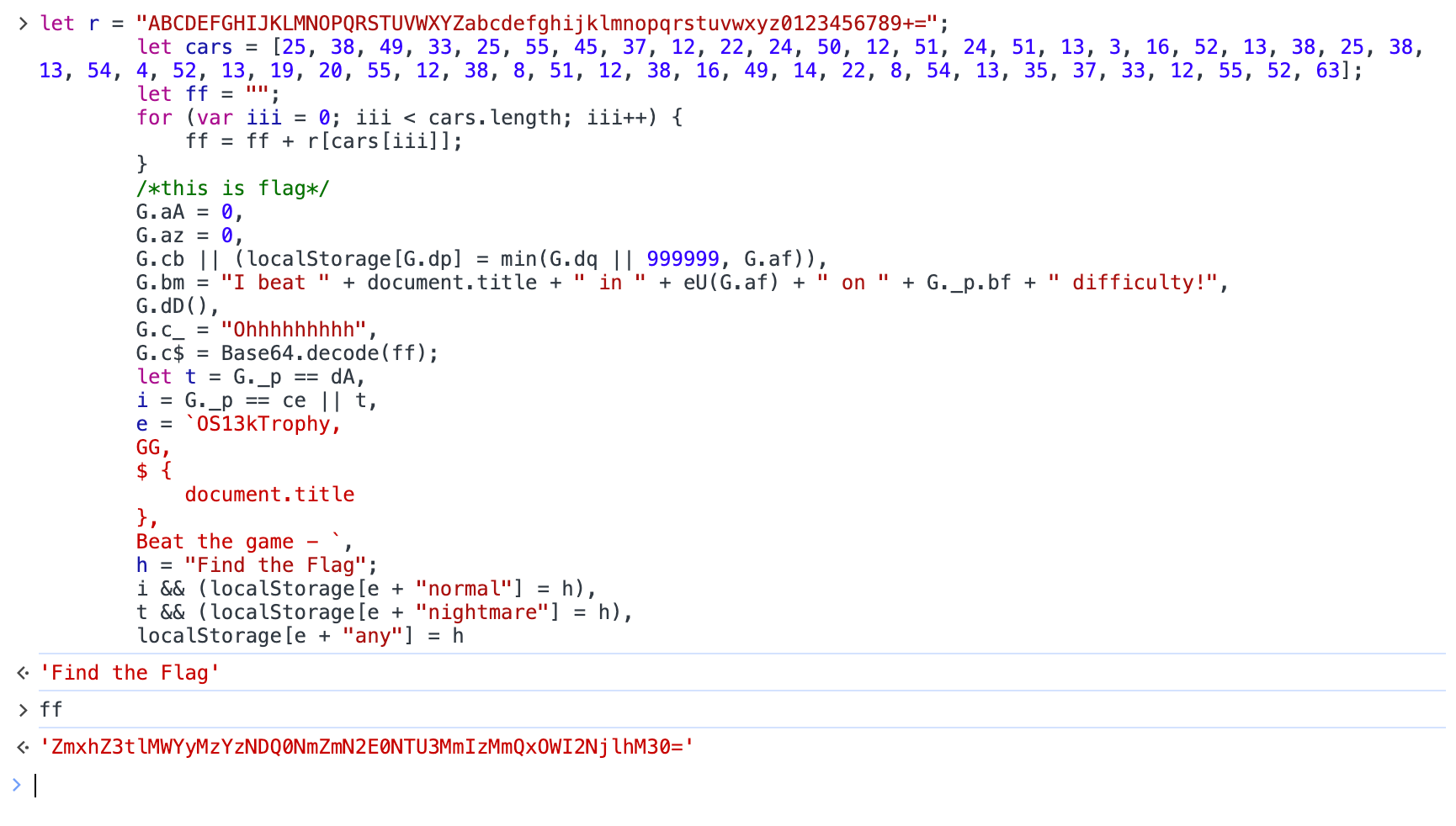
1 | ZmxhZ3tlMWYyMzYzNDQ0NmZmN2E0NTU3MmIzMmQxOWI2NjlhM30= |
base64 解码得 flag
Misc - 啊吧啊吧的数据包
通过筛选 POST 请求发现有 shell 交互:
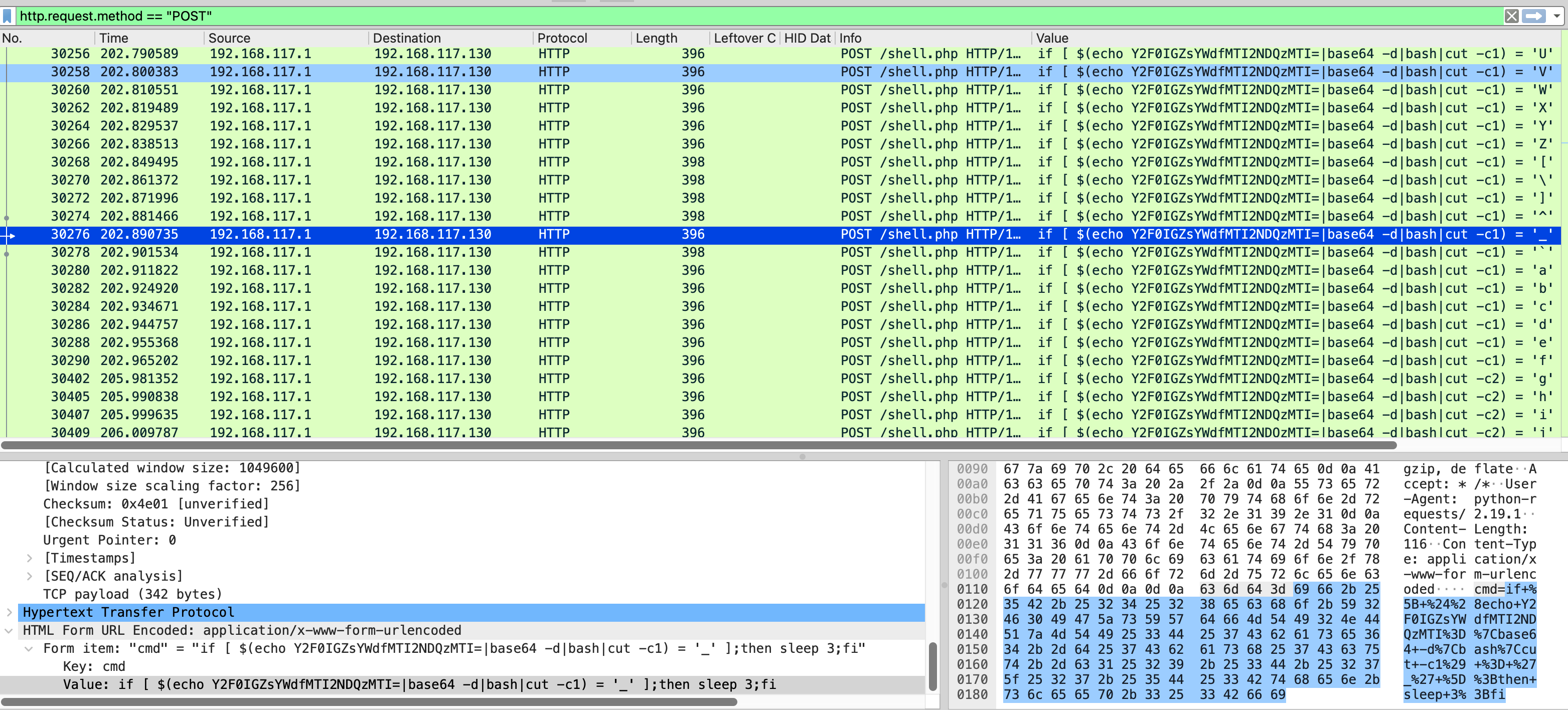
解码 base64 发现这是一个查看 flag 的操作
1 | echo Y2F0IGZsYWdfMTI2NDQzMTI= | base64 -d |
再结合后面的命令,这个 shell 在逐个字符爆破 flag,采用时间盲注,那么筛选这一段的 http 流数据(30147 - 35661),导出为 csv 便于 python 处理,删掉多余的列之后,保留 value 和时间, 写脚本处理即可:
1 | #!/usr/bin/python3 |
Misc - 我应该去爱你
扔到 Audacity 里看频谱,这玩意考眼神:
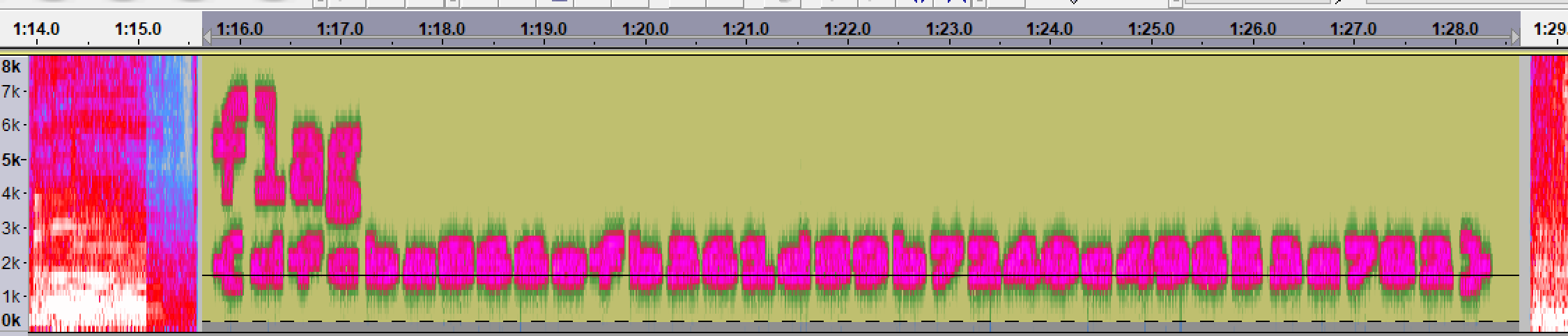
猜了好几遍才猜对,眼神不行了😅
1 | flag{dfcba866efb361d89b7240c49653a782} |
Misc - 简单编码(补)
- 比赛日下午脑子一团浆糊,最后十几分钟才意识到这玩意是不是 二进制和八进制
- 然后写脚本,寄在这个根据长度判断是二进制还是八进制(但凡判断条件里头加上个
=就出 flag 了)- 出来的字符串先 base64 解码,然后 base32 解码,最后 hex2str
1 | import base64 |
Misc - 神秘的 base(补)
- 👴🏻之前没用过 base 换表,不晓得怎么改,找 b64decode 源码改了一通也不行
- 原来只需要 translate 就行😅
- 后续补的脚本:
1 | import base64 |
Crypto - 小试牛刀
给的密文:
1 | ipfm\x82Kj]p~l?\x82ogw\x85mt[K\x8br\x97 |
猜测是根据 flag{} 进行变换的
那么找规律发现:
1 | In [11]: ord('f') - ord('i') |
写解题脚本得到 flag:
1 | d = b"ipfm\x82Kj]p~l?\x82ogw\x85mt[K\x8br\x97" |
Reverse - 人生模拟(补)
- 👴🏻好久不用 Ghidra 的 patch,给忘了导出要选 ELF(👴🏻选的Binary,👴🏻脑子瓦特了),就说怎么 patch 的程序直接执行不了
简单看了看程序逻辑,猜测 flag 会在 FUN_0040350f 函数中打印出来,想要执行到这里必须要活到 60 岁,在主函数中的 while 循环里的 FUN_00403914 函数应该是获取当前的年龄:
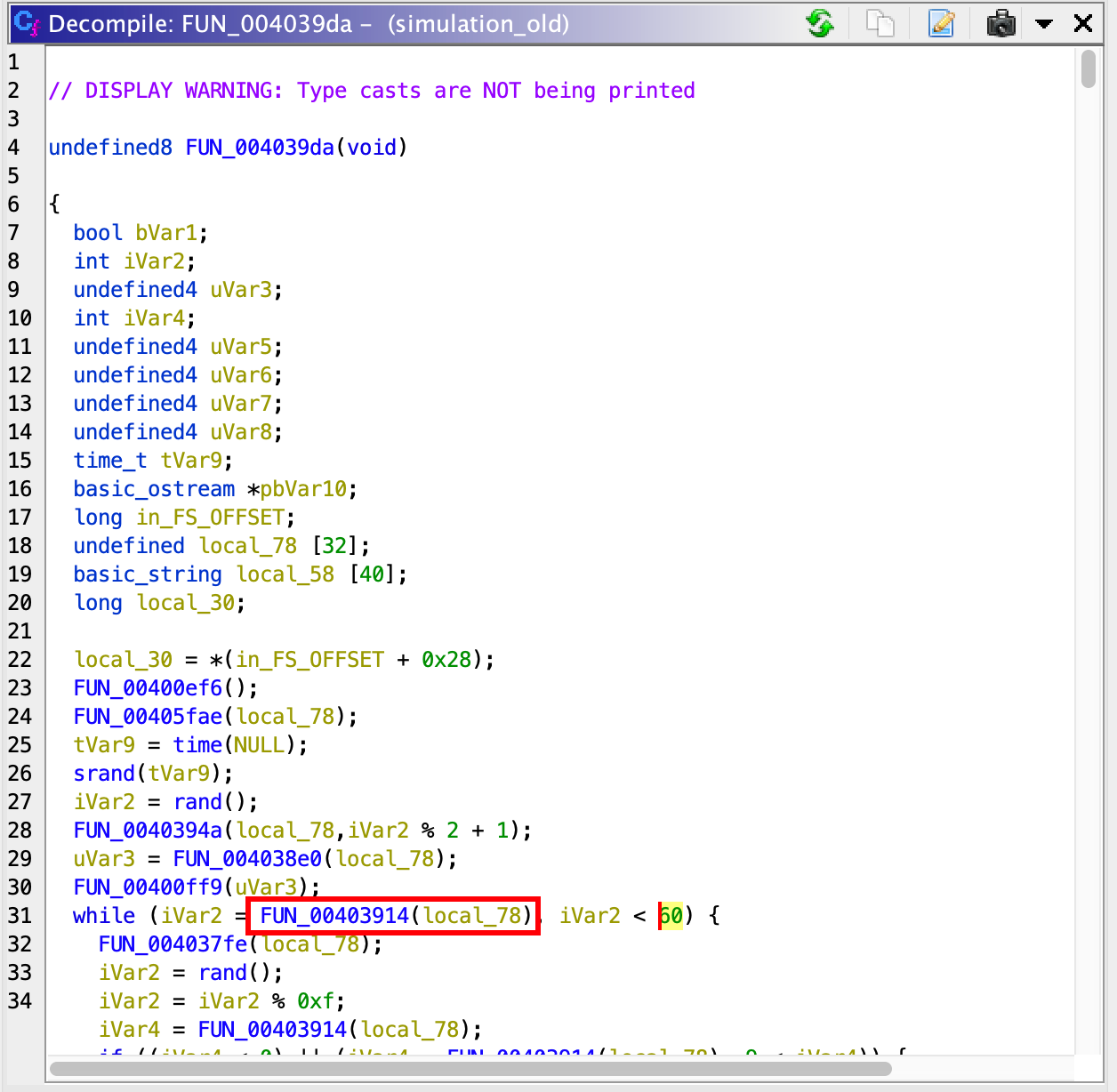
这个函数长这样:
1 | 00403914 55 PUSH RBP |
那直接 patch, 直接返回 60:
1 | 00403914 55 PUSH RBP |
然后 FUN_0040350f 函数里有这样的条件判断:
1 | if ((((0 < param_2) && (0 < param_3)) && (0 < param_4)) && |
直接把对应条件判断指令反过来写, 改完:
1 | if ((((true) && (true)) && (true)) && (((true && (param_1 == 60)) && (local_f0 != 0x11120c94)))) |
Patch 完直接导出 ELF 文件, 运行之后崩溃在了 0x4035de 处(idiv rcx, 此时 rcx 是 0),直接 nop 掉,重新导出运行就能拿到flag:
1 | ./simulation2 |